The travel-only Gmail account: A practical proposal for digital privacy at the US border
This article is cross-posted to Medium and Hacker Noon.
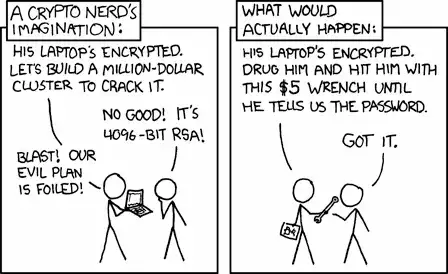
xkcd’s well-circulated wrench scenario, pictured above, is demonstrated hauntingly well by this week’s story of Sidd Bikkannavar, a US-born NASA engineer who was coerced into breaching the security of his government-issued phone in order to enter the United States. US Customs and Border Patrol detained Bikkannavar, who like me has Global Entry, upon entering and demanded he unlock his cell phone for searching. About 30 minutes later, he got his phone back and was free to go. He’s still unaware what took place during that time.
What follows is my plan, and the thinking behind it, for avoiding such an invasion myself. (TL/DR: Wipe your phone before getting on the plane.)
Amendments A’schendments
But his right to remain silent should protect his passcode, you say? Bikkannavar’s dilemma, at the time he was ordered to unlock his phone, was this: he was in a locked holding cell with federal agents who told him he had to unlock his phone before being free to go.
Even for a native-born US citizen, a standoff with CBP is both intimidating and, at the very least (and I do mean very least), inconvenient. My suspicion is that for most people, a missed connection is threat enough to comply. The risk of indefinite detention followed by a long legal battle and possibly criminal charges is a life-altering martyrdom most of us aren’t practically or emotionally equipped for.
But at the same time, one’s cell phone and laptop are portals to the world. In my case, through the use of a password manager, all of my devices can, once all data has been decrypted, access my financial records, intimate conversations I’ve had with my spouse, perhaps even communications I’ve had with therapists going back decades. The prospect of being forced to surrender my phone’s passcode is more than just abhorrent, it’s an intimate and personal violation with real consequences for my well-being.
Deniable Encryption: An ideal solution
There is, as it turns out, a type of encryption for exactly this scenario. It’s called deniable encryption and the idea is that adversaries wouldn’t know whether they have access to all the information on a device or not.
One elegant way it could work would be through two passcodes. One passcode would encrypt only a little data, perhaps showing a web browser open to Yahoo Sports, while another more secret passcode would get into the real thing, complete with private information. Adversaries would have no way of knowing which passcode you gave them, nor would they be able to determine whether a second (or third) passcode even exists. (This is similar, but not identical, to the concept of a duress code.)
Unfortunately, modern operating systems leak so much data all over the place that deniable encryption is almost a fool’s errand. And if you’re used to the convenience of using mainstream consumer gadgets, it’s a lost cause.
Enter the ironic cloud loophole
Since at least the Snowden disclosures, conventional wisdom has been that your data is safest in your immediate physical possession, rather than the cloud, because while general warrants can (apparently) be issued against cloud data, media in one’s possession is immune to anything but an old fashioned physical search.
But in the case of a border crossing, the cloud actually becomes a safer place, provided your laptop or cell phone doesn’t have access to it. As long as there’s no nexus between your device and the cloud, you aren’t crossing the border with that cloud data, so it’s not subject to search.
A painful solution
Assuming you trust encryption, then, there is an obvious, though inconvenient, way to protect yourself. Since cloud data is immune from a border search, you can encrypt your data, store it in the cloud, wipe your devices prior to crossing, then restore your data after crossing in relative safety.
This is, obviously, an arduous process. Most of us have a plethora of apps, photos, and work projects we bring around with us and restoring all of those is going to take more than a few minutes at baggage claim.
Even worse, traveling is when we use our devices most. We entertain ourselves on planes, find amenities at airports, and even change itineraries during travel using those devices.
To ameliorate some of the pain, I am creating special “travel-only” Google accounts and user profiles on my devices, which will remain active while I travel. Besides keeping me connected during international travel, having my devices logged to something should also deflect any retalia — I mean — “extra scrutiny” arising from possessing factory-reset devices.
For recovery, I’ll need to make sure my zero-knowledge backups are fully restorable from only my own memory. This means I’ll be disabling two-factor authentication for my cloud storage provider, using passphrases, and testing the restoration process before trusting it.
Will it work?
Since before the election, I’ve been traveling abroad. Next week, I’m coming home to Colorado for a bit. I intend to follow this plan and report back with the results.
I believe I’m unlikely to be singled out for a search, but if it happens, I’ll let you know how it goes. I’ll also be reporting back on the practicality of my new protocol, along with any tips I come up with along the way. Hopefully it’ll all go smoothly.
While I’m optimistic that an inevitable Supreme Court decision will render all of this legally unnecessary, it’s worth keeping in mind that a precedent is only very useful if agents both know it and choose to obey it. Also, our bad ideas tend to be exported, so I wouldn’t be surprised to learn about some other authoritarian regimes following America’s shameful lead around the world.
But that’s fodder for another time.
For now, safe travels and I’ll check in next week. Cheers.
Update: I did cross into the United States unmolested my CBP. Read my followup article where I share what I’ve learned.